 Let me be clear: I am not a fan of Bernie Sanders’ politics. I do not believe socialism is a good economic system, nor that it is compatible with the United States Constitution. However, I do agree in principle with one idea that Bernie Sanders symbolized: that the political system in the United States is corrupt and tilted in favor of the rich and politically powerful. While at first I was diametrically opposed with what Bernie Sanders stood for, I eventually gained a respect for the man and the movement that grew around him. I believe that many of his supporters are less true socialists and rather hold more anti-establishment ideals. I can definitely see why someone who claimed they were going to level the political playing field received so much support. Therefore I was a bit surprised when Bernie Sanders seemed to sell out and support Hillary Clinton as nominee of the Democratic Party. He had just spent many months painting her as everything he stood opposed to and then it was revealed that the Democratic National Committee conspired to ensure Hillary Clinton was their nominee. Having some time to ponder the situation, I’ve come to two conclusions.
Let me be clear: I am not a fan of Bernie Sanders’ politics. I do not believe socialism is a good economic system, nor that it is compatible with the United States Constitution. However, I do agree in principle with one idea that Bernie Sanders symbolized: that the political system in the United States is corrupt and tilted in favor of the rich and politically powerful. While at first I was diametrically opposed with what Bernie Sanders stood for, I eventually gained a respect for the man and the movement that grew around him. I believe that many of his supporters are less true socialists and rather hold more anti-establishment ideals. I can definitely see why someone who claimed they were going to level the political playing field received so much support. Therefore I was a bit surprised when Bernie Sanders seemed to sell out and support Hillary Clinton as nominee of the Democratic Party. He had just spent many months painting her as everything he stood opposed to and then it was revealed that the Democratic National Committee conspired to ensure Hillary Clinton was their nominee. Having some time to ponder the situation, I’ve come to two conclusions.
Bernie is Doing What He Must
First, Bernie Sanders is being an extremely smart politician. If he had bucked the DNC and withheld his support for Hillary Clinton, he would be politically finished. The DNC is too powerful for him to stand against. His best chance at moving his political agenda forward was to ally with Hillary Clinton and give her his full support. In exchange, she claims she will adopt some of his ideals and the DNC will keep Bernie at the forefront of their party. Bernie is doing exactly what he needs to do to remain politically relevant. I can not blame him as a politician for doing what he is doing. He has worked to bring himself mainstream visibility in national politics and he wants to leverage that base of support the best way he can. However, Bernie supporters are not beholden to Hillary Clinton or the DNC. They can continue Bernie’s mission even if he can not currently do so himself. Obviously he can no longer tell his supporters to not vote for Hillary Clinton, but it doesn’t take much to read between the lines on how he really feels about her.
The problem with supporting Hillary Clinton is that no one can trust her any farther than they can throw her. Of course she says now that she will advocate the policies that Bernie Sanders promoted. She needs the votes of Bernie Sanders’ supporters to get elected! Like Barack Obama said in 2008, Hillary Clinton will say anything to get elected. But what happens after she gets elected? She will say and do anything it takes to keep political favor and reward those who helped get her elected, which if you believe Bernie Sanders, include a lot of Wall Street and big money donors. She is as just as likely to align with Republicans (as her husband did in the 90’s) if that will help her get re-elected or help her contributors. If I were a a Hillary Clinton supporter, I would be scared to death that she will keep any of the promises she is giving now – and so should Bernie Sanders supporters. There is nothing keeping her from dropping you like a bad habit if she gets elected. She won’t need you in the next election.
Bernie Sanders 2020?
My second conclusion is that for Bernie Sanders to ever have any chance at the presidency, Hillary Clinton can not be elected president this year. The reality for Bernie Sanders supporters is that the Senator is 75 years old. He would have already been the oldest president ever elected this year. Four years from now at 79 years old is realistically his last chance at becoming president. If Hillary Clinton or any Democratic Party member (Hillary Clinton might be impeached if she is elected president) is the president 4 years from now there’s no way Bernie Sanders will have an opportunity to run. Unless a Hillary Clinton presidency is an absolute train wreck of unprecedented proportions, he can’t honestly run against the party he supports. His only chance is for someone other than a Democratic Party member to be president in 2020 so he can mount a viable campaign. If you are a true Bernie Sanders supporter, electing Hillary Clinton will kill any chance he has of ever becoming president and she likely will suffocate his agenda to appease her big money supporters. A vote for Hillary Clinton is shooting yourself in the foot and also excusing the DNC shutting for out Bernie Sanders’ campaign and his supporters.
But Donald Trump!
Ok, I get it that you can not support Donald Trump. I’m not asking you to vote for him. In fact I’m not voting for him. There are ways besides voting for Trump to show that you are not satisfied with the establishment candidates in this presidential election. You also get an opportunity to punish the DNC for disenfranchising your vote.
The simplest thing you can do is vote for a third-party candidate of your choice. The most likely options are Gary Johnson of the Libertarian Party and Jill Stein of the Green Party. The simple choice is that if you are more anti-establishment, Gary Johnson is your man and if you identify as a true socialist then Jill Stein better represents you. But do your own research to make your own conclusions. That being said, I will add that if any third party gets over 5% of the popular vote this election cycle, it gets them automatic ballot access in the next election plus significant federal funding which will start them on equal footing with the establishment parties. They can then put more resources towards campaigning instead of fighting tooth and nail to get on the ballots in all 50 states. Certainly having more political voices can only help us all, much like Sanders did in his presidential bid. The most popular third party candidate thus far is Gary Johnson, so if you want to help third parties get more viability, then a vote for Gary Johnson will be the most likely way to make that happen. If one third party can break the political glass ceiling, then it will pave the way for others as well.
If you honestly can not vote for a third party, then a write in vote is an option, but do note that write-in votes will not help any third-party gain viability. You could also not vote, but that is truly wasting your voice. The establishment parties are more than happy if you do not vote because then it means your vote simply doesn’t exist and they get to keep the status quo. A vote for a third party or even a write-in vote is an unmistakable message that you are not happy with the political establishment. A non-vote simply disappears and doesn’t really say anything at all. So whatever you do vote in some way, just not for Hillary Clinton.
A lot of you will say that a third-party vote is still a vote for Donald Trump. I respectfully disagree, but even if we accept this assumption, it is actually more helpful for Bernie Sanders if Trump were elected than Hillary Clinton. If Donald Trump is as bad as you think he is, then it makes it all the more likely that Bernie Sanders would be the Democratic Party nominee next election cycle. As a Bernie Sanders supporter, you believed that the best chance of defeating Trump was Bernie Sanders. If you believed it then, you must believe that one term of a Trump presidency will make it even more likely for Bernie Sanders to win the next election. Yes, I agree this option stinks, but you were robbed of your opportunity this election. If you want any chance at getting Bernie elected president, you may need to put up with 4 years of Donald Trump. If anything this is Hillary Clinton and the DNC’s fault so how can you reward them with your vote?
Who do You Really Believe in?
It simply comes down to this for Bernie Sanders supporters: what do you believe about Hillary Clinton? Do you believe what Barack Obama said in 2008 and what Bernie Sanders said in the primaries about her corruption and big money influences, or do you believe she will actually keep her word after she’s taken your vote? If you trusted your candidate back then, know that he is doing what he can as a politician to keep his influence by aligning with Hillary Clinton now, but that doesn’t mean you must. Send a message to the DNC that they can not get away with disenfranchising your vote and you will not support Hillary Clinton this election so that Bernie Sanders can have one last chance at becoming president next election.
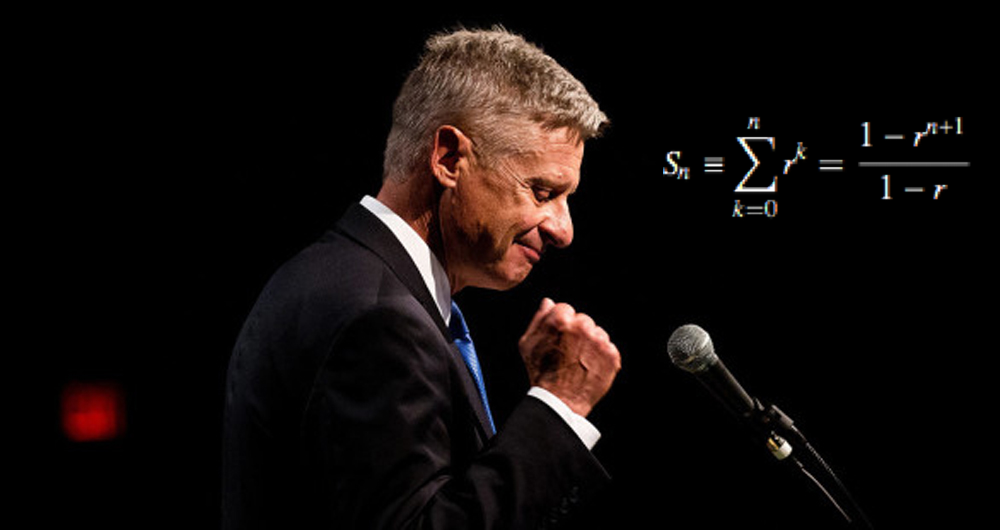 It should be no surprise to anyone that the level of voter dissatisfaction with the candidates presented to us by the establishment parties is at an all-time high. A huge number of people do not want to vote for either Donald Trump or Hillary Clinton. So what are they to do? An ever increasing number of people are considering voting for a third party candidate, but when discussing it with others, they start to doubt the validity of voting for a third party.
It should be no surprise to anyone that the level of voter dissatisfaction with the candidates presented to us by the establishment parties is at an all-time high. A huge number of people do not want to vote for either Donald Trump or Hillary Clinton. So what are they to do? An ever increasing number of people are considering voting for a third party candidate, but when discussing it with others, they start to doubt the validity of voting for a third party.

 In analyzing the Apple and FBI court case over the iPhone used by a San Bernadino terrorist, it has become quite obvious that many people are not completely comprehending the entirety of the facts. Unfortunately for Apple, I believe the complexity of the situation is hurting their position in the public eye. The FBI’s side of the issue has generally become overly-simplified. “Apple needs to unlock the iPhone of a terrorist,” is all that many people comprehend. I believe it has been hard for most people to understand the nuances of Apple’s defense. As with anything relating to technology, people can get easily bewildered by explanations of complex topics. Given an overly simplistic and one-sided viewpoint, it really is no wonder that there is much confusion over the issue. When people are not clear on a subject, they tend to fall back to whatever side feels the “safest.” In a case like this, it is no wonder public opinion appears to lean towards the side of “national security.” As proof of this, all one has to do is consider the fact that no candidate from either the Democratic or
In analyzing the Apple and FBI court case over the iPhone used by a San Bernadino terrorist, it has become quite obvious that many people are not completely comprehending the entirety of the facts. Unfortunately for Apple, I believe the complexity of the situation is hurting their position in the public eye. The FBI’s side of the issue has generally become overly-simplified. “Apple needs to unlock the iPhone of a terrorist,” is all that many people comprehend. I believe it has been hard for most people to understand the nuances of Apple’s defense. As with anything relating to technology, people can get easily bewildered by explanations of complex topics. Given an overly simplistic and one-sided viewpoint, it really is no wonder that there is much confusion over the issue. When people are not clear on a subject, they tend to fall back to whatever side feels the “safest.” In a case like this, it is no wonder public opinion appears to lean towards the side of “national security.” As proof of this, all one has to do is consider the fact that no candidate from either the Democratic or 
 It’s no secret I have a great interest in the technology industry, especially when it comes to the topic of Apple. I also have a great interest in history and politics, hence the name and topic of this blog. So when the situation with
It’s no secret I have a great interest in the technology industry, especially when it comes to the topic of Apple. I also have a great interest in history and politics, hence the name and topic of this blog. So when the situation with 
 It’s an issue that has been brewing over the last year-and-a-half. When Apple introduced iOS 8 in the fall of 2014, one particular feature had privacy advocates cheering. That same feature had certain law enforcement officials seething.
It’s an issue that has been brewing over the last year-and-a-half. When Apple introduced iOS 8 in the fall of 2014, one particular feature had privacy advocates cheering. That same feature had certain law enforcement officials seething.  Yes, you read the title correctly. Contrary to what most people think, the surprising truth is that within the context of the seemingly endless gun control debate, the Second Amendment simply doesn’t matter. It has virtually no relevance and most people who base gun control discussions around the Second Amendment are wasting their time. The Second Amendment even has very little significance in any conversations about the right to bear arms. Does this sound crazy? Good. I’ve got your attention and now we can really get to the core of the gun control discussion.
Yes, you read the title correctly. Contrary to what most people think, the surprising truth is that within the context of the seemingly endless gun control debate, the Second Amendment simply doesn’t matter. It has virtually no relevance and most people who base gun control discussions around the Second Amendment are wasting their time. The Second Amendment even has very little significance in any conversations about the right to bear arms. Does this sound crazy? Good. I’ve got your attention and now we can really get to the core of the gun control discussion.