 I’m not usually an overtly “patriotic” type of person. Two years ago my oldest daughter played the national anthem at one of her first football games as part of her high school marching band. It happened to be 9/11. I did feel something stir inside me. It probably was because on September 11th, 2001 the birth of my first child was imminent and my life was changing forever. So these events are forever intertwined in my mind.
I’m not usually an overtly “patriotic” type of person. Two years ago my oldest daughter played the national anthem at one of her first football games as part of her high school marching band. It happened to be 9/11. I did feel something stir inside me. It probably was because on September 11th, 2001 the birth of my first child was imminent and my life was changing forever. So these events are forever intertwined in my mind.Remembering 9/11, Sixteen Years Later
 I’m not usually an overtly “patriotic” type of person. Two years ago my oldest daughter played the national anthem at one of her first football games as part of her high school marching band. It happened to be 9/11. I did feel something stir inside me. It probably was because on September 11th, 2001 the birth of my first child was imminent and my life was changing forever. So these events are forever intertwined in my mind.
I’m not usually an overtly “patriotic” type of person. Two years ago my oldest daughter played the national anthem at one of her first football games as part of her high school marching band. It happened to be 9/11. I did feel something stir inside me. It probably was because on September 11th, 2001 the birth of my first child was imminent and my life was changing forever. So these events are forever intertwined in my mind.Bernie Sanders’ Last Chance for President
 Let me be clear: I am not a fan of Bernie Sanders’ politics. I do not believe socialism is a good economic system, nor that it is compatible with the United States Constitution. However, I do agree in principle with one idea that Bernie Sanders symbolized: that the political system in the United States is corrupt and tilted in favor of the rich and politically powerful. While at first I was diametrically opposed with what Bernie Sanders stood for, I eventually gained a respect for the man and the movement that grew around him. I believe that many of his supporters are less true socialists and rather hold more anti-establishment ideals. I can definitely see why someone who claimed they were going to level the political playing field received so much support. Therefore I was a bit surprised when Bernie Sanders seemed to sell out and support Hillary Clinton as nominee of the Democratic Party. He had just spent many months painting her as everything he stood opposed to and then it was revealed that the Democratic National Committee conspired to ensure Hillary Clinton was their nominee. Having some time to ponder the situation, I’ve come to two conclusions.
Let me be clear: I am not a fan of Bernie Sanders’ politics. I do not believe socialism is a good economic system, nor that it is compatible with the United States Constitution. However, I do agree in principle with one idea that Bernie Sanders symbolized: that the political system in the United States is corrupt and tilted in favor of the rich and politically powerful. While at first I was diametrically opposed with what Bernie Sanders stood for, I eventually gained a respect for the man and the movement that grew around him. I believe that many of his supporters are less true socialists and rather hold more anti-establishment ideals. I can definitely see why someone who claimed they were going to level the political playing field received so much support. Therefore I was a bit surprised when Bernie Sanders seemed to sell out and support Hillary Clinton as nominee of the Democratic Party. He had just spent many months painting her as everything he stood opposed to and then it was revealed that the Democratic National Committee conspired to ensure Hillary Clinton was their nominee. Having some time to ponder the situation, I’ve come to two conclusions.
Bernie is Doing What He Must
First, Bernie Sanders is being an extremely smart politician. If he had bucked the DNC and withheld his support for Hillary Clinton, he would be politically finished. The DNC is too powerful for him to stand against. His best chance at moving his political agenda forward was to ally with Hillary Clinton and give her his full support. In exchange, she claims she will adopt some of his ideals and the DNC will keep Bernie at the forefront of their party. Bernie is doing exactly what he needs to do to remain politically relevant. I can not blame him as a politician for doing what he is doing. He has worked to bring himself mainstream visibility in national politics and he wants to leverage that base of support the best way he can. However, Bernie supporters are not beholden to Hillary Clinton or the DNC. They can continue Bernie’s mission even if he can not currently do so himself. Obviously he can no longer tell his supporters to not vote for Hillary Clinton, but it doesn’t take much to read between the lines on how he really feels about her.
The problem with supporting Hillary Clinton is that no one can trust her any farther than they can throw her. Of course she says now that she will advocate the policies that Bernie Sanders promoted. She needs the votes of Bernie Sanders’ supporters to get elected! Like Barack Obama said in 2008, Hillary Clinton will say anything to get elected. But what happens after she gets elected? She will say and do anything it takes to keep political favor and reward those who helped get her elected, which if you believe Bernie Sanders, include a lot of Wall Street and big money donors. She is as just as likely to align with Republicans (as her husband did in the 90’s) if that will help her get re-elected or help her contributors. If I were a a Hillary Clinton supporter, I would be scared to death that she will keep any of the promises she is giving now – and so should Bernie Sanders supporters. There is nothing keeping her from dropping you like a bad habit if she gets elected. She won’t need you in the next election.
Bernie Sanders 2020?
My second conclusion is that for Bernie Sanders to ever have any chance at the presidency, Hillary Clinton can not be elected president this year. The reality for Bernie Sanders supporters is that the Senator is 75 years old. He would have already been the oldest president ever elected this year. Four years from now at 79 years old is realistically his last chance at becoming president. If Hillary Clinton or any Democratic Party member (Hillary Clinton might be impeached if she is elected president) is the president 4 years from now there’s no way Bernie Sanders will have an opportunity to run. Unless a Hillary Clinton presidency is an absolute train wreck of unprecedented proportions, he can’t honestly run against the party he supports. His only chance is for someone other than a Democratic Party member to be president in 2020 so he can mount a viable campaign. If you are a true Bernie Sanders supporter, electing Hillary Clinton will kill any chance he has of ever becoming president and she likely will suffocate his agenda to appease her big money supporters. A vote for Hillary Clinton is shooting yourself in the foot and also excusing the DNC shutting for out Bernie Sanders’ campaign and his supporters.
But Donald Trump!
Ok, I get it that you can not support Donald Trump. I’m not asking you to vote for him. In fact I’m not voting for him. There are ways besides voting for Trump to show that you are not satisfied with the establishment candidates in this presidential election. You also get an opportunity to punish the DNC for disenfranchising your vote.
The simplest thing you can do is vote for a third-party candidate of your choice. The most likely options are Gary Johnson of the Libertarian Party and Jill Stein of the Green Party. The simple choice is that if you are more anti-establishment, Gary Johnson is your man and if you identify as a true socialist then Jill Stein better represents you. But do your own research to make your own conclusions. That being said, I will add that if any third party gets over 5% of the popular vote this election cycle, it gets them automatic ballot access in the next election plus significant federal funding which will start them on equal footing with the establishment parties. They can then put more resources towards campaigning instead of fighting tooth and nail to get on the ballots in all 50 states. Certainly having more political voices can only help us all, much like Sanders did in his presidential bid. The most popular third party candidate thus far is Gary Johnson, so if you want to help third parties get more viability, then a vote for Gary Johnson will be the most likely way to make that happen. If one third party can break the political glass ceiling, then it will pave the way for others as well.
If you honestly can not vote for a third party, then a write in vote is an option, but do note that write-in votes will not help any third-party gain viability. You could also not vote, but that is truly wasting your voice. The establishment parties are more than happy if you do not vote because then it means your vote simply doesn’t exist and they get to keep the status quo. A vote for a third party or even a write-in vote is an unmistakable message that you are not happy with the political establishment. A non-vote simply disappears and doesn’t really say anything at all. So whatever you do vote in some way, just not for Hillary Clinton.
A lot of you will say that a third-party vote is still a vote for Donald Trump. I respectfully disagree, but even if we accept this assumption, it is actually more helpful for Bernie Sanders if Trump were elected than Hillary Clinton. If Donald Trump is as bad as you think he is, then it makes it all the more likely that Bernie Sanders would be the Democratic Party nominee next election cycle. As a Bernie Sanders supporter, you believed that the best chance of defeating Trump was Bernie Sanders. If you believed it then, you must believe that one term of a Trump presidency will make it even more likely for Bernie Sanders to win the next election. Yes, I agree this option stinks, but you were robbed of your opportunity this election. If you want any chance at getting Bernie elected president, you may need to put up with 4 years of Donald Trump. If anything this is Hillary Clinton and the DNC’s fault so how can you reward them with your vote?
Who do You Really Believe in?
It simply comes down to this for Bernie Sanders supporters: what do you believe about Hillary Clinton? Do you believe what Barack Obama said in 2008 and what Bernie Sanders said in the primaries about her corruption and big money influences, or do you believe she will actually keep her word after she’s taken your vote? If you trusted your candidate back then, know that he is doing what he can as a politician to keep his influence by aligning with Hillary Clinton now, but that doesn’t mean you must. Send a message to the DNC that they can not get away with disenfranchising your vote and you will not support Hillary Clinton this election so that Bernie Sanders can have one last chance at becoming president next election.
Mathematical Proof Gary Johnson Can Win – The Power of Two!
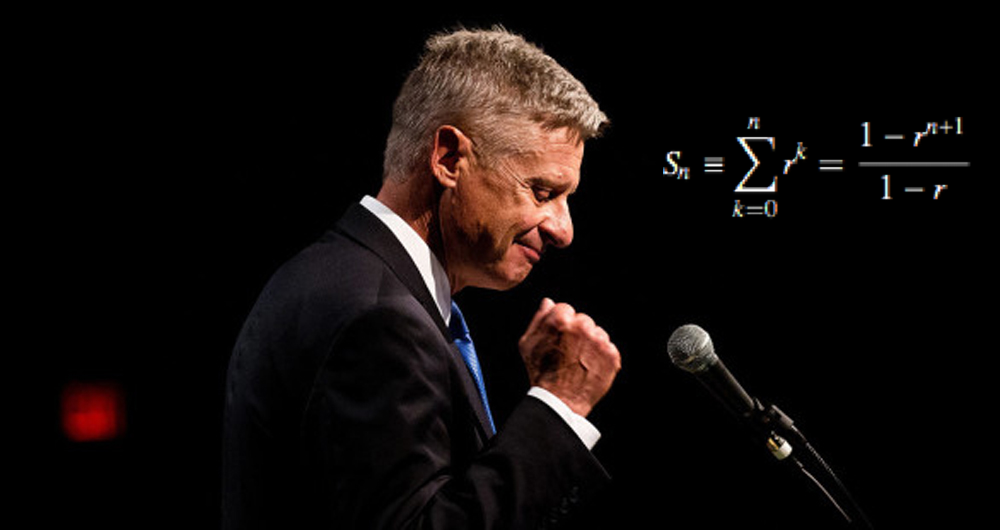 It should be no surprise to anyone that the level of voter dissatisfaction with the candidates presented to us by the establishment parties is at an all-time high. A huge number of people do not want to vote for either Donald Trump or Hillary Clinton. So what are they to do? An ever increasing number of people are considering voting for a third party candidate, but when discussing it with others, they start to doubt the validity of voting for a third party.
It should be no surprise to anyone that the level of voter dissatisfaction with the candidates presented to us by the establishment parties is at an all-time high. A huge number of people do not want to vote for either Donald Trump or Hillary Clinton. So what are they to do? An ever increasing number of people are considering voting for a third party candidate, but when discussing it with others, they start to doubt the validity of voting for a third party.
Sadly, the number one objection to voting for a third party is that people think they would be wasting their vote on a candidate that can’t win. With thinking like that, it virtually guarantees that no third party will ever become relevant and the political status quo will remain. How can a candidate ever get enough support to win if people are waiting first for everyone else to get on the bandwagon?
I’m sure you’ve all heard that if one person shares an idea with two people and those two people each tell two more people, and so on, that idea will spread very quickly. Mathematically speaking, this is called geometric (or exponential) growth. When doubling something each time, the math formula is based upon exponents of the number two, or in other words, the power of two. I bring it up now to end the narrative that a third party presidential candidate, specifically Gary Johnson, can not possibly win the presidential election and hopefully help convince people to vote their conscience and bring about political change in this country.
It’s Simple Math
For purposes of this exercise, let’s ignore the electoral college and simply surmise that it will take approximately 50 million votes to win in a three-way race (it would probably be closer to 47 million, but 50 is a nice round number). This assumes there would be about 130 million votes total, which would about equal the highest ever number of popular votes in a presidential election: the 131 million cast in 2008. Mathematically speaking, if we started with a single voter convincing two other voters, it would take only 25 “generations” of subsequent voters convincing other voters to reach over 67 million votes, far more than the 50 million needed. (The formula for computing the exponential sum of a number taken to a certain power is basically to calculate one power higher and subtract 1. So if 226 = 67,108,864, the sum of the powers of 2 up to the 25th power is 226 – 1.)
To put a timeframe around this calculation, what if we concluded that one voter could convince two other voters in a single day? Then it would only take 25 days to generate enough votes for a presidential candidate to win. If we slowed down the process and assumed it took two days to convince two voters, then that is still only 50 days needed to convince enough voters for a presidential win in a three-way race. Pushing the timeframe out to three days equals 75 days, which at the time of this writing is almost exactly the amount of time left before the election. That is plenty of time for enough people to become convinced to vote for any candidate, let alone one that already has growing popularity like Gary Johnson.
If you feel that convincing two voters every few days is not realistic, realize that we are not starting at one single voter. Gary Johnson received 1.2 million votes in 2012 (with ballot access in only 48 states) – the most ever for a Libertarian Party candidate. If we round down and make the starting point just 1 million voters, then it would only take 5 generations to reach 64 million votes, much more than the 50 million he would need. If we started with one million voters today, at the pace of convincing only two voters every week, that would only require five weeks. If we stretch that out to every two weeks, that would still be fast enough to get enough votes to win – with time to spare. Certainly persuading two voters over the course of a week or two must seem feasible.
Still not convinced? Consider these facts:
- Gary Johnson’s base of support has been growing steadily since he was officially nominated as the candidate of the Libertarian Party back on May 29th – over 12 weeks ago. As it became clear that Donald Trump and Hillary Clinton were to be the official candidates of the Republican and Democratic parties 4 and 5 weeks ago, interest in third party candidates including Gary Johnson increased significantly. Given the exponential growth possibilities, that is a lot of time passed in which voters may have already been convinced.
- If various polls are accurate (and they generally are skewed against third party candidates), with Gary Johnson approaching 15% of the vote, that is currently about 19 million out of 130 million votes. With that base of support, if those 19 million people each convinced just two other voters, that ALONE would be enough to go over the 50 million need to win in a three-way race.
- If Gary Johnson is allowed to participate in the presidential debates, a lot of potential voters could be convinced “spontaneously,” adding to the base of people who could convince other voters.
- Gary Johnson already has ballot access in all 50 states this election cycle. There’s no reason people won’t be able to vote for him if they so choose.
- What if one voter could convince three other voters? Suddenly, the number of generations shrink significantly. Assuming one voter to start, it would take just 15 generations to reach over 43 million votes, which is close to the rounded-up 50 million number needed (a 16th generation would reach over 129 million in theory). Assuming one million voters to start, it would only take 3 generations to reach 81 million votes, obviously well more than needed. At 19 million voters to start, convincing just three people each (a single generation) would be enough for 76 million votes, once again significantly more needed to win in a three-way race.
- In this day and age of social media, just how many other people can one person help convince? They don’t call it “going viral” for nothing. Suddenly, convincing just two or three other voters seems too easy. What if one voter could convince four or five other voters? Or more?
Now obviously, convincing someone to vote for a candidate isn’t a simple mathematical formula. It takes more than just merely telling someone about a candidate – although with the high negative numbers the two establishment candidates have this election cycle, it might not take all that much! This article is not proof that Gary Johnson is GOING to win. It simply is proof that it is entirely POSSIBLE for virtually anyone to get enough support to win a presidential election in a relatively short timeframe IF voters are willing to personally convince a few other voters. If we even allow for imperfect geometric growth on the power of two, there is plenty of time left at this point in this election cycle to convince enough voters for Gary Johnson to win outright, not to mention that this process has been going on for at least a few months and there is already momentum on his side.
You’ve Got to Do Your Part
Of course, convincing other voters requires people taking part in conversations and discourse – and that is the entire point! It does require some work and people need to be willing to put themselves out there a little bit. However, if you aren’t satisfied with the political status quo and want to effect substantive change, you need to put a little effort into it. If you feel like it is impossible to help a third party candidate win, that you can’t do much as one person, simply try to convince at least two other people to vote third party and make sure to tell them to each convince at least two other people. Feel free to share this article with them for emphasis. As this article shows, you might just start the ball rolling on real political change in this country. Even if you can’t vote yourself but you are politically inclined, as many teenagers and immigrants may be, you can help influence the votes of others. The two or more people you convince can start a tidal wave.
As I mentioned at the start of this article, when you are telling people about third party candidates like Gary Johnson, the first thing you’ll likely hear is that the person likes the idea of a third party candidate, but they don’t think they can actually win. Therefore they don’t want to waste their vote. Hopefully the information in article can be your first response to this objection and you can start to change a few minds. By using the Power of Two, it only takes a few people convincing a few other people and so on …
9th U.S. Circuit Court of Appeals Ruling is Elitist, Sexist, Homophobic, and Racist

This is how the state of California and the 9th U.S. Court of Appeals view the free people they supposedly serve
The 9th U.S. Circuit Court of Appeals has ruled that the 2nd Amendment does not protect the right of individuals to carry concealed weapons. Certainly I have much to say on the implications that this ruling has on our rights and freedoms. However, that is the low-hanging fruit. I prefer to look a little deeper. In reviewing the ruling, I think many people are overlooking the inherent elitism that the court ruling implies, possibly going as far to be called sexist, homophobic, and dare I say racist.
The basic crux of the matter at hand are that people in California are only legally allowed to carry concealed weapons if they are granted a permit. Part of being approved for this permit is dependent on the applicant proving that “good cause exists” for carrying a concealed weapon. Each county in California is allowed to define what exactly “good cause” means for the applicants in their jurisdiction. One of the counties in question, Yolo County, does not explicitly define “good cause,” but only gives examples of what they consider to be valid reasons to carry a concealed weapon:
- Victims of violent crime and/or documented threats of violence.
- Business owners who carry large sums of cash or valuable items.
- Business owners who work all hours in remote areas and are likely to encounter dangerous people and situations.
Additionally, both Yolo and San Diego County, the other named county in the lawsuit against the state of California, explicitly define that “self protection and protection of family” or “simply fearing for one’s personal safety alone” are not valid reasons for carrying a concealed weapon. So let’s further examine these “good causes,” shall we?
Elitism is Alive and Well in Big Government
Basically what these counties are saying, and by extension the state of California and the 9th U.S. Circuit Court of Appeals endorse, is that the life of a person or their family are not “good causes” worth protecting, but large sums of cash or “valuable” items are. So cash and material items are more “valuable” than human life according to these various big government entities. Besides the inherent condescension of a government imposing where and how the people they serve may exercise their own rights, not allowing people to defend their own lives unless they have “valuable” cash or items smacks of unabashed elitism. If one is looking for a situation where real privilege is handed out, look no further than the state of California and their concealed carry legislation. Apparently, only certain lives are privileged enough to defend themselves.
The state of California and the United States government is basically telling women that their bodies and health are not valuable enough to protect against rapists. How sexist of them. Talk about a war on women, big government believes women aren’t capable enough to determine for themselves when they have a “good cause” to protect themselves from violent sexual predators. The same goes for homosexuals. Big government in California does not allow the LGBT community to decide for themselves when they think they posses “good cause” to safeguard themselves from violent people. Are the state of California and the United States government homophobic? Sure sounds like it.
However, if you are a business owner, and only a business owner, you apparently are “likely to encounter dangerous people and situations.” Now, I wonder exactly how the state of California defines “dangerous people.” Would they be people who live in certain areas? Maybe those areas would include inner cities? Don’t people of minority status live in inner cities? Racists!
Now, I admit that this last point may be a bit of a stretch. But, I would be willing to bet that if the records of who was given concealed carry permits were reviewed and for what circumstances, it could be interpreted in a way that would show tendencies to give permits to people who were more affluent and non-minority. I wonder if anyone has this information or if the state of California would be willing to divulge such data?
So what do you think? Do you like the fact that certain governments think they know better than you where and how you may protect yourself or your family? Or are you happy that they consider cash and material items to be more valuable than you and your family’s lives?
Democratic Candidates Totally Lame on Apple, FBI

Having no position is basically the same as siding with the FBI.
Last week I wrote an article taking the Republican presidential candidates to task for not understanding the broad implications of the Apple and FBI situation. I didn’t consider at the time what the two Democratic candidates’ positions were. So I did a little reading and found that while the Democratic candidates were not firmly on the side of the FBI as the Republicans were, they too didn’t seem to grasp the possible ramifications of Apple being forced to comply with the FBI order. In some way, their weak-kneed refusals to choose a stance are perhaps even worse than what the Republicans stated. I’ll explain why.
Bernie Sanders said he is on “both” sides of the issue. He said he is fearful of “Big Brother” but he also worries about another terrorist attack. Ultimately he says that he believes that middle ground can be reached. At first glance this seems like a perfectly balanced, rational answer, but it shows a tacit ignorance of the technical issues involved. Political compromise will not work in the real world of data encryption.
Hillary Clinton basically offered the exact same answer as Sanders. She also fears abuse of encryption backdoors by “authoritarian regimes,” but believes that there must be a way to find a solution that both keeps data secure and allows law enforcement access. Again, seemingly reasonable but only if one does not understand the underlying technical issues.
Wishy-Washy Pandering
The answers given by both Democratic candidates are political cop-outs. They are not true position statements. While I appreciate the fact that at least these two candidates aren’t calling for Apple to comply with the FBI order, by not specifically siding with Apple, they are leaving the door open for some sort of “compromise.” In this situation, to call for compromise is to implicitly end up on the side of the FBI, which is to stand against individual privacy and security.
The reality of strong encryption is that *ANY* sort of backdoor weakens the encryption protocol to the point of insecurity. Any weakness will eventually be exploited. I find it hard for anyone who does not understand the underlying technical aspects of strong encryption, let alone government officials or political candidates, to propose solutions that verge on pure fantasy. The type of compromise that the the Democratic candidates floated (which is basically what the FBI director wants) is what is termed the “magic pony” solution because it is more wishful thinking than technical reality. I do not know of a single cryptographic expert who would claim otherwise, and even publications like the MIT Technology Review agree that there can be no technical middle ground on strong encryption.
I stated earlier that the Democratic candidates’ responses are potentially worse than the Republican candidates’ positions. By floating false solutions, the Democrats are setting the stage for people to believe that a “compromise” is possible. There is no more dangerous position to hold than one which deceives people into a false sense of security. If people believe that a solution can be created that allows for truly secure encryption that law enforcement can decrypt, they are going to be sorely disappointed when the final political solution shows itself to be insecure. At least we know where the Republicans stand and we can fight their positions with no pretense. When a candidate shows no position or shows a proclivity towards political compromise, we may not know what we will end up with until after they are elected and it is too late.
Understanding Apple’s Side of Their Fight with the FBI
 In analyzing the Apple and FBI court case over the iPhone used by a San Bernadino terrorist, it has become quite obvious that many people are not completely comprehending the entirety of the facts. Unfortunately for Apple, I believe the complexity of the situation is hurting their position in the public eye. The FBI’s side of the issue has generally become overly-simplified. “Apple needs to unlock the iPhone of a terrorist,” is all that many people comprehend. I believe it has been hard for most people to understand the nuances of Apple’s defense. As with anything relating to technology, people can get easily bewildered by explanations of complex topics. Given an overly simplistic and one-sided viewpoint, it really is no wonder that there is much confusion over the issue. When people are not clear on a subject, they tend to fall back to whatever side feels the “safest.” In a case like this, it is no wonder public opinion appears to lean towards the side of “national security.” As proof of this, all one has to do is consider the fact that no candidate from either the Democratic or Republican party has shown explicit support for Apple.
In analyzing the Apple and FBI court case over the iPhone used by a San Bernadino terrorist, it has become quite obvious that many people are not completely comprehending the entirety of the facts. Unfortunately for Apple, I believe the complexity of the situation is hurting their position in the public eye. The FBI’s side of the issue has generally become overly-simplified. “Apple needs to unlock the iPhone of a terrorist,” is all that many people comprehend. I believe it has been hard for most people to understand the nuances of Apple’s defense. As with anything relating to technology, people can get easily bewildered by explanations of complex topics. Given an overly simplistic and one-sided viewpoint, it really is no wonder that there is much confusion over the issue. When people are not clear on a subject, they tend to fall back to whatever side feels the “safest.” In a case like this, it is no wonder public opinion appears to lean towards the side of “national security.” As proof of this, all one has to do is consider the fact that no candidate from either the Democratic or Republican party has shown explicit support for Apple.
That being said, I believe Apple could be doing a better job of simplifying the perception of their case in the court of public opinion. Unless someone wants to study Apple’s public statements in detail, it can be hard to get to the heart of Apple’s defense and understand why their position speaks to more broad-ranging issues than simply the data on one terrorist’s phone. So to help simplify Apple’s position, I have read Tim Cook’s open letter, watched his interview with ABC, read every page of Apple’s Motion to Vacate, and just this morning, Apple’s prepared statement to the House Judiciary Committee so that I can explain and clarify Apple’s position plus impart why it is so important for everyone to understand.
If you want a quick summary, Apple’s position basically states:
- The FBI’s order goes far beyond any precedent set before.
- It is unduly burdensome to Apple and the technology industry in general
- The precedent set would give government virtually unlimited power to trample on personal liberties well outside of the scope of this case
- Finally the FBI order is quite simply illegal. If anything, this is a matter for congress to legislate, not for the FBI or a judge to decide.
In a nutshell, the FBI’s actions could end up having far-reaching repercussions that devastate the very freedom they are supposed to be protecting. If you’d like a more through explanation, keep reading.
Apple’s Defense Explained
First, it can not be stressed enough that the FBI’s order is NOT a simple warrant to search for some data. Nor is it a request for Apple to do something they can easily do or have done before. It is not as simple as “pushing a few buttons” or just removing some code. If it were so straightforward, Apple would have already complied, as they have in the past and have cooperated so far in this situation. Complying with the FBI’s order will be a massively complex technical undertaking for Apple, taking hundreds or thousands of man-hours to complete, plus potentially a significant amount more resources to maintain after the fact. Never has a private company ever been forced to go through such lengths on an investigation they are not a direct party to. Additionally, the FBI unilaterally decided to change the iCloud password of the terrorist’s account prior to consulting with Apple. Why they did this is not known at this time, but by doing this they wasted a great opportunity to have access to the data on the phone without needing to go through extraordinary measures. It is entirely possible the FBI could have avoided this situation altogether had they not make such a grievous error.
Second, the veritable Pandora’s box that would be opened by complying with the FBI order would be an incredible burden to not only Apple but potentially much of the technology industry. While the FBI claims this would be a one-time request on a single phone, the reality is that many law enforcement departments are already lining up to make the same request as the FBI – and the FBI themselves already have several other cases in waiting! Besides being a significant and costly burden for Apple or any other company with similar products, the creation and maintenance of an insider hacking tool has serious implications on the security of American technology products. If companies can be forced to hack their own products, would they actually be able to create truly secure devices anymore? The monumental burden for companies to create, maintain, and keep secure these self-inflicted hacking tools would be unlike any ever sustained before. Companies are used to protecting trade secrets from other companies, but can they honestly be asked to protect hacking tools that criminals and foreign espionage would no doubt target?
Now the two points I have brought up above are somewhat arbitrary. They primarily speak to the undue burden that the government would place on Apple and other technology companies. It is not hard to see that someone who takes a hardline on national security could brush away these arguments with a simple, “tough luck” rationale. However, the next two points are what I believe are the meat and potatoes of Apple’s position, which truly should be the position of anyone who is concerned with protecting privacy and individual liberties in this country, as well as national security.
Apple’s third argument contends that legal enforcement of the FBI’s order implies that they can literally enforce any request of any kind on any company or individual as long as they claim it is “necessary” for the purposes of law enforcement. There would be virtually nothing that could not be requested, including forcing a company to create encryption backdoors. This is quite literally the definition of conscription, impressment, or involuntary servitude. While the FBI may not be technically asking for an encryption backdoor in this particular case, it is in essence a legal back door to eventually forcing technology companies to cripple the security of their products for the convenience of law enforcement. It is precisely this legal back door that privacy and liberty advocates should be the most concerned about, especially because it could be so broadly applied to almost any company in any industry as well as private individuals.
This argument dovetails right into perhaps Apple’s most powerful defense, namely that the federal government simply does not have the authority to make such a request. It is categorically outside the power given to them through the Constitution by we the people. Therefore such a request is plain illegal. I don’t know how anyone could justify the federal government violating the very Constitution they are sworn to defend and uphold. Tim Cook himself said, “To oppose your government … on something where we are advocating on civil liberties which they are supposed to protect, it is incredibly ironic.”
Why YOU Should Care About What Apple is Defending
While the FBI and the Obama administration may be semantically correct that this particular request is just about one iPhone, it should be obvious that what the FBI is trying to force Apple to comply with has ramifications far beyond just a single investigation. Absolutely nothing would stop the FBI or other law enforcement agencies from pursuing the same strategy on other cases. If the software Apple were forced to develop were ever leaked into the public, criminals and foreign governments would have a dangerous tool at their disposal. The odds of the software leaking would increase every single time another agency ordered its use.
As Tim Cook reiterated many times during his televised interview, this isn’t about one iPhone, it is about the future. He brought up a great point that my wife especially took notice of: your smartphone likely has more personal information about you, including the location of your family and children, than anything else in the world. The security of people’s data on their smartphones is no trivial matter. If the FBI’s actions end up endangering the private data on millions of people’s phones, that is potentially a disaster of monumental proportions. When viewed as a public safety issue, Apple has just as much of an argument on the side of national security as the federal government does.
The bottom line is that if you care about the security of your most private data: your finances, health data, and even the safety of your family, you must realize that what the FBI is asking for is very dangerous. It would be undermining the extensive security precautions Apple and other technology companies have been refining in addition to subverting many of the principles of individual liberties that this country was founded on. If we are working to protect this country from terrorists who want to destroy our freedoms and principles that we hold dear, why would we accept our own government destroying them instead?
Republican Candidates Screw the Pooch on Apple, FBI

The party of small government? Apparently not when it comes to technology issues.
The topic of the Apple vs FBI situation came up during the Republican Presidential Debate on CNN last night. To my dismay, all the candidates of the supposed party of small government took a hardline, big government stance against Apple. I guess I shouldn’t be too surprised, as I expected this position from a couple of the candidates, but it did confirm my fears on how the situation is being misperceived amongst many in the public. I would have loved to see at least one candidate take a principled stand against the FBI (et tu, Ben Carson?), which is one reason I really wish Rand Paul had stayed in the race to provide a contrast when the other Republicans stray into the weeds on certain issues. That being said, let’s do a quick run-down on each candidate’s comments:
Donald Trump: The frontrunner was not actually asked about this situation during this debate, but based on his earlier comments, we know Donald Trump’s position (and I’m paraphrasing): Terrorist BAD … FBI GOOD … Apple make me ANGRY! But seriously, his position is based on a simple misunderstanding of the situation, which it seems most of the candidates shared as I’ll explain below.
Marco Rubio: As he usually is, Marco Rubio seemed very rehearsed in his response to the question. He delivered the best zinger of the night saying that “Apple doesn’t want to do it, because they think it hurts their brand. Well let me tell you, their brand is not superior to the national security of the United States of America.” He correctly pointed out that the FBI’s request was not an encryption backdoor but just a way to crack the password on one phone. So it was clear that he had been well coached on the topic, but unfortunately those who were advising him focused on the FBI’s side of the argument, ignoring the positions Apple has brought up. Rubio however was clear that he did not support encryption backdoors in general, so perhaps his team hasn’t had a chance to review Apple’s court filing that was released earlier in the day. Perhaps he will change his position upon further view.
Ted Cruz: For being such a strict Constitutionalist and generally a principled defender of individual liberties, I was most dismayed that Cruz didn’t take a more nuanced stance on the situation. He basically thought that Apple should comply with a legal court order, clearly missing the point that the the legality of the court order is in question – which is truly the heart of the issue. He at least did clarify that he does not support government enforcing encryption backdoors, but he apparently is not aware of the full implications of the FBI’s orders on our rights and freedoms. I’m hoping that once he gets a chance to read Apple’s court filing, he will modify his stance.
Ben Carson: Ben Carson has been a fairly principled small-government advocate and one of the least hardline when it comes to national security issues. So it was odd to hear him say that he believed Apple should comply with the FBI order. However, I also got the impression that Carson was simply not up to speed on the issue. Which again, if one only listens to the soundbites coming from the FBI side of things, Apple just needs to “click a few buttons” and the FBI will have their data. But it is far more complicated than that. Carson was basically just repeating what the other candidates said which was that they believed Apple should comply with a legal court order. Well, sure they should, but this court order is possibly illegal. I’m sure Rand Paul would have pointed that out.
John Kasich: I think John Kasich is just trying to emulate Donald Trump the longer the campaign drags on. Kasich did not actually express an opinion whether or not Apple should comply with the FBI order, but instead just stuck out his chest and admonished President Obama for not forcing Apple and the FBI to come up with a solution. He said that if he were president, he would lock the two sides into a room and not let them out until they reached an agreement. Well, Mr. Kasich, that may work for someone who is an employee of the government under your charge, but Tim Cook is a private citizen, Apple is a private company, and locking up Cook or any Apple employee would basically be kidnapping or unlawful detention. So Kasich showed he doesn’t understand the complexity of the situation either and in some ways, his answer was the worst of any of the candidates. Not all issues can be solved through political compromise, especially when core issues of liberty and privacy are at stake. Going along to get along might make good politics, but it doesn’t protect our freedoms very well.
Let Me Spell it Out for the Candidates
The bottom line is that it was clear none of the candidates understood the technical underpinnings of this situation. This is not a simple warrant to search for some data. If it were that easy, Apple would have already complied, as they have in the past and already have cooperated so far in this situation. There are four main points to consider in Apple’s defense. They are not hard, so even a politician should have no trouble comprehending them:
First, the action the FBI is requesting is not as simple as pushing a few buttons. It will be a complex technical undertaking for Apple to be able to comply with the FBI’s request, taking hundreds or thousands of man-hours to complete, and potentially a significant amount more to maintain after the fact. As I mentioned already, Apple has already complied with all lawful requests from the FBI and has even turned over data in their possession from previous iCloud backups of the iPhone in question. Clearly it’s not like Apple isn’t complying with all reasonable and legal requests. Additionally, had the FBI not unilaterally made the decision to change the iCloud password prior to consulting with Apple, they would have been able to make the iPhone initiate a new backup and avoid this situation altogether.
Second, the veritable Pandora’s box that would be opened by complying with the FBI order would be tremendously burdensome to not only Apple but potentially much of the technology industry. While the FBI claims this would be a one-time request on a single phone, the reality is that many law enforcement departments are already lining up to make the same request as the FBI – and the FBI themselves already have at least four other cases in waiting! Besides just being a significant and costly burden for Apple or any other company with similar products, the creation and maintenance of an insider hacking tool has serious implications on the security of American technology products. If companies can be forced to hack their own products, would they be able to create truly secure devices anymore? The significant burden for companies to create, maintain, and keep secure these self-inflicted hacking tools would be unlike any ever endured before. Companies are used to protecting trade secrets from other companies, but can they honestly be asked to protect hacking tools that criminals and foreign espionage would no doubt target?
Third, the implications of the FBI’s order is that they can literally enforce any request of any kind on any company or individual as long as they claim it is “necessary” for the purposes of law enforcement. There would be virtually nothing that could not be requested, including forcing a company to create encryption backdoors. This is quite literally the definition of conscription, impressment, or involuntary servitude. While the FBI may not be technically asking for an encryption backdoor in this particular case, as Marco Rubio pointed out, it is in essence a legal back door to eventually forcing technology companies to cripple the security of their products for the convenience of law enforcement. It is precisely this back door that small-government advocates should be the most concerned about and why I’m surprised they had not yet caught on to this critically important aspect of the situation.
Which dovetails right right into the final argument, that the federal government simply does not have the authority to make such a request. It is simply outside the power given to them through the Constitution by we the people. Therefore such a request is illegal. I don’t know how anyone could justify the federal government violating the very Constitution they are sworn to defend and uphold. I wish Apple were pushing this point harder, because then I believe it would make it crystal-clear to those who claim to support small government and privacy rights.
It is not surprising to me that the campaigns of these candidates are not up to speed on complex technical issues. A technology advisor is not something that has been part and parcel of a political campaign in the past. But with technology issues becoming more and more of a part of modern politics, perhaps it is time for politicians to consult with technology experts prior to drafting policy positions? I’m certainly willing to lend my expertise to any of these campaigns, if they are willing to listen.
Tim Cook, Apple, Encryption, the FBI, and a Chance to Change the World
 It’s no secret I have a great interest in the technology industry, especially when it comes to the topic of Apple. I also have a great interest in history and politics, hence the name and topic of this blog. So when the situation with Apple and the FBI came to a head last week, I knew I had to write about it. In case you’ve been living under a rock, the FBI is attempting to force Apple to help them break into the iPhone of a San Bernadino terrorist. Apple is currently refusing to comply with the order, claiming the FBI’s specific request would jeopardize the safety of their customers’ data and set a bad precedent for the ability of government to force technology companies to compromise the security of their own products.
It’s no secret I have a great interest in the technology industry, especially when it comes to the topic of Apple. I also have a great interest in history and politics, hence the name and topic of this blog. So when the situation with Apple and the FBI came to a head last week, I knew I had to write about it. In case you’ve been living under a rock, the FBI is attempting to force Apple to help them break into the iPhone of a San Bernadino terrorist. Apple is currently refusing to comply with the order, claiming the FBI’s specific request would jeopardize the safety of their customers’ data and set a bad precedent for the ability of government to force technology companies to compromise the security of their own products.
There are strong opinions on both sides. There are people who believe in strong privacy rights and applaud Apple for standing up against what they perceive as government overreach. The other side can’t understand why anyone would want to prevent law enforcement from investigating a terrorist. Both sides make good points at certain times, which makes the situation far from black and white. This is why I took my time in crafting this article so I could study all the points involved and give a well-reasoned and through examination. So strap on your seat belts because you are about to go on a wild ride through the topics of technology and politics!
The Issues Are Conflated
There has been a long-running debate in techno-political circles regarding strong encryption technology and law enforcement. Simply put, modern encryption technology like that used by Apple and other smartphone manufacturers work so well that no one is able to crack it – not even law enforcement agencies of the federal government nor the manufacturers themselves. Obviously law enforcement wants to be able to decrypt data from technology devices that are part of criminal investigations. Government officials are suggesting that technology companies should create “backdoors” into their products so that law enforcement can decrypt their products. They are also threatening to create regulations that will force them to do so if they do not comply voluntarily. It is against this backdrop that the current predicament with Apple and the FBI is taking place.
However, this situation with Apple, the FBI, and the iPhone of the San Bernadino terrorist is NOT the same as the above debate. In this instance, the FBI is not attempting to force Apple to create or use an encryption technology with a backdoor. Even if they were, it could not help them in this particular scenario because the iPhone in question is already encrypted with virtually unbreakable technology. Rather, what the FBI is asking of Apple is to create a modified operating system that would remove safeguards against brute-force password attacks for this particular iPhone. The FBI claims that if Apple were to comply, they could crack the password on the iPhone and decrypt the data without a backdoor.
Apple contends that complying with this order would require compromising the security precautions they have built into their products. They claim that by doing so they would put at great risk the privacy and security of the data of all their customers. They are calling what the FBI is requesting a “backdoor.” However, while Apple is technically correct in describing the FBI order as exploiting a backdoor, it is NOT the same type of encryption backdoor that has been the subject of much debate that I described above. The FBI has responded that they are not asking for a backdoor to encryption (in which they are technically correct), but rather just a one-time way to crack a password on one particular iPhone.
Let me be clear. I wholeheartedly believe that the idea of government enforcing encryption backdoors is a terrible idea and additionally they have no authority to mandate this. However, in this case the backdoor already seems to exist. The FBI claims they have discovered a way to work around the passcode protections on an iPhone and Apple’s response seems to have confirmed that this exploit would work. Apple is not fighting a battle on the front of encryption technologies in this instance. It is an entirely, albeit related, confrontation here.
It is clear that Apple is waging a larger war. Apple has been very steadfast on the encryption technology debate, staunchly rebuffing government suggestions for backdoors and even calling out the Obama administration for not taking a stand on the side of privacy rights. Perhaps that is why they are conflating the issues at hand. Maybe they believe that these issues are similar enough and they should just combine them for public debate. I can not blame them for taking this tactic. To some degree, the idea that government can force a technology company to exploit a security hole in their own product is related to the idea that government can force a technology company to purposely create backdoors into their products. But at the same time, I feel that Apple is possibly doing a disservice to the cause in the way they are approaching this fight.
Law vs Opinion
There are two battles being fought. One is playing out in an actual courtroom. The other is being wrangled in the court of public opinion. Certainly in a society with a government of the people, public opinion is extremely important. With the support of enough people, government can be compelled to take or not take certain actions. However, there is danger in popular democracy. Just because a majority of people believe in a certain way does not mean they are right. The opinion of the people can also be swayed by those with power and influence. Additionally, the perception of popular opinion can be skewed to fit a narrative. This is all especially true when dealing with complex technical topics, given that most people will base their opinions upon only brief soundbites.
Apple is taking a great risk by conflating the larger encryption debate with the San Bernadino iPhone issue. It is entirely possible that the situation plays out against Apple in either the courts of law or of public opinion. If that happens, it could have negative ramifications for protecting strong encryption technologies in general. The problem is that currently Apple’s main argument seems to be in the realm of the theoretical. They are saying that the FBI’s actions could have serious ramifications. It could set a very bad precedent. However, there is nothing clear-cut that would immediately happen if Apple is forced to comply with the FBI’s court order.
It is easy for naysayers to dismiss a theoretical argument when there is a real-world situation at hand. I fear it will be all too easy for those on the side of the FBI to wrap their messaging around the tragedy that took place in San Bernadino and sway the courts as well as popular sentiment. Once they have this momentum on their side, it could create new support (or at least the perception of it) for restricting the type of encryption technologies companies like Apple can use. If the FBI gets their way, it would be a simple task for proponents of encryption backdoors to argue that the San Bernadino situation is an example of why law enforcement needs an easy way to decrypt anyone’s device. If I can imagine this scenario, it is certain that political strategists have already played out this chess game in their minds.
While I don’t mind Apple bringing the issues at hand to the public’s attention, I believe that Apple should also be taking a stronger approach. An approach based in law that is not bound to the whim of popular opinion or that of politicians. If they were to do this, Apple has a great opportunity to strike at the root of not only the encryption debate, but also possibly tackle much broader issues impacting privacy and freedom as well.
Should Not vs May Not
It’s one thing to point out why the government should not do something, as Apple’s strategy seems to be so far. However, it is entirely more powerful to point out that government is not allowed to do something based on constitutional law. It’s the difference between a philosophical discussion and a mathematical equation. The first is open to interpretation while the second is based on hard and fast rules that simply can not be broken. People may not agree on the meaning of life, but 1+1 always equals 2.
If one believes that any law passed by a majority vote in a legislature is valid, then theoretical arguments rule the day. Politicians can rationalize almost any argument in their favor and they certainly have. For example, if legislators can argue that a farmer growing wheat on their own land for their own use should be considered interstate commerce AND they can get the Supreme Court to agree with them, then politicians can rationalize just about anything. While this scenario may sound like fantasy, it is sadly a very real case that was decided in 1942 (Wickard v. Filburn).
Political power knows no bounds. In the United States, the only thing standing in the way of unbridled government action are the limits upon it defined in the Constitution. Politicians can not make the case they are going to break constitutional law in order to accomplish something. Obviously that would not fly with the public. This is why they will go through mental gymnastics to try to fit something under their authority as they did in Wickard v. Filburn. Astute readers will point out that politicians have been very successful at rationalizing/ignoring laws for a long time and I definitely agree. The problem is that there have been too few situations where a defendant has challenged the government to prove their authority. While Wickard v Filburn was decided in favor of unfettered government, more recently United States v. Lopez in 1995 was the first significant decision since 1942 that ruled government had overstepped its bounds. So there is still some glimmer of constitutional limits upon government power that exist and I think Apple has an incredible opportunity to make history if they are willing to go full bore against government overreach in this situation.
How Apple Could Make Legal History
If Apple truly wants to close the door on government attempting to control the use of strong encryption, as well as other related government infringements on privacy and intrusions into personal technology, they need to force the government’s hand. They need to make the federal government explain where they claim to derive the authority to force a private company to comply with the type of request they have made of Apple. Going further, Apple could challenge the idea that government may simply pass a law that would require technology companies to comply with these types of orders including the creation of encryption backdoors. So how could Apple accomplish this?
To start, we must understand how the FBI is currently attempting to force Apple to comply with their order. The FBI has cited a law called the All Writs Act of 1789 as their justification to force Apple into compliance. Yes, this law was written in 1789, the first year of George Washington’s presidency. If there were any other law on the books that the FBI could have cited that would have more specifically forced Apple to comply, they would have used it. But there is not, which is why the FBI must fall back to using the All Writs Act. Here is the entire text:
28 U.S. Code § 1651 – Writs
(a) The Supreme Court and all courts established by Act of Congress may issue all writs necessary or appropriate in aid of their respective jurisdictions and agreeable to the usages and principles of law.
(b) An alternative writ or rule nisi may be issued by a justice or judge of a court which has jurisdiction.
(June 25, 1948, ch. 646, 62 Stat. 944; May 24, 1949, ch. 139, § 90, 63 Stat. 102.)
A “writ” is basically a legal order. The All Writs Act of 1789 states that federal courts may issue all writs necessary or appropriate, which is a fairly broad statement. However, it then says that those writs must be agreeable to the usages and principles of law. Ok, so federal courts may issue legal orders but those orders must be lawful themselves. How do we know if a writ is lawful? Well, we could consult with an attorney to comb through volume after volume of federal codes to find if certain writs fall within the authority of the courts … OR we could consult for ourselves the supreme law of the land to see if the federal government has any jurisdiction to begin with. The great thing about the US Constitution is that it was written in plain language so anyone can read and understand it. Since the founders intended this to be a government of the people, they didn’t want it to be a government that only lawyers could understand.
The fundamental question is does the federal government, or more specifically a federal court, have the authority to force a company like Apple to create a method to break into one of its products? A lot of people think that this particular court order is a very simple warrant like most warrants, which allow law enforcement to search a particular place. As I’ve explained already, this case is nowhere near that simple. The FBI already has possession of the phone in question and the phone technically belongs to the employer the terrorist worked for, which has already given permission for the phone to be searched. Also, Apple does not have in their possession any of the data currently on the phone. In fact, Apple has already provided the FBI copies of old backups from this iPhone that were stored on their iCloud servers. Apple claims they had already complied with every legal request from the FBI to this point. What this particular court order asks Apple to do is create a modified version of the iPhone operating system that would work to effectively bypass some security features.
So can a judge of a federal court make such an order? The judicial power of the United States is defined entirely in Article III of the Constitution, which itself is comprised of just three short sections. Section 1 merely defines that the judicial power shall be vested in one supreme court and inferior courts as Congress may establish. Skipping to Section 3, it only defines the crime of treason and that congress can declare the punishment for treason within a few limitations. The meat of the judicial power is contained within Section 2 of Article III and all it really says is where judicial power extends. Part of Section 2 says that this power extends to all cases arising under the Constitution and the laws of the United States, which is sufficient enough for discussion of this particular situation. The real question is does the Constitution and/or any other law of the United States cover this particular situation? If laws do not apply, then the courts should have no authority.
Does United States law cover the Apple and FBI situation? Obviously a crime has been committed and the FBI has taken jurisdiction, investigating the San Bernadino murders as an act of foreign terrorism. If the federal government has the authority to investigate and prosecute terrorism, that power applies to the subjects of the investigation. But Apple is not a subject of this investigation. Other than the data they had in their possession that they’ve already turned over, Apple has no involvement in this case. They are simply the manufacturer of a product that was possessed by a criminal. We don’t even know if the phone was used to communicate with anyone involved in the crime or if there is any data on the phone that would be useful in the investigation. For most intents and purposes, Apple is an independent third party to this investigation. It is one thing for an independent party to offer to help law enforcement or to help when requested. It is another thing entirely for a third party to be forced into servitude of the government, especially when that servitude stands to materially harm that party.
As I said above, the FBI has no option other than to use the All Writs Act of 1789. Because they are using such an old law that is quite vague in its definition, we must fall back onto more foundational law, so once again we consult the United States Constitution. The way the federal government works (at least, the way it is supposed to work), all legal authority must flow from the Constitution, as it is the supreme law of the land. The Constitution lays out some very specific limited powers vested in the legislative body of the federal government, as defined in Article I, Section 8. If one were to read the short text of that section, one would not find any specific legal authority related to this situation. Nowhere does it say that congress has the power to pass laws forcing companies to help the government in a criminal investigation. Obviously it does not say anything about computerized technology, given that this document was written in the late 18th century. However, just because something did not exist in the 1700’s, does not mean the government automatically gets authority over it when it comes into existence. We the people must grant the government any authority before it can legally exercise power. So it would appear from a cursory review of the Constitution that the federal government would not have authority to force Apple to comply with its request at this time, nor would they even have the authority to pass a law requiring such things in the future. But this situation can’t be so simple, could it?
Earlier I brought up Wickard v. Filburn as an example of the type of rationalization government can use to justify their jurisdiction over an area of law. This was not a random example. I brought it up because it will likely be very relevant as this situation plays itself out over time. The federal government has become quite astute at using the “interstate commerce clause” as justification for nearly any and every law passed in the last 80 years that can in any slight way be shown to somehow involve “commerce.” The government’s go-to play would be to cite the Commerce Clause as the root of their power to regulate Apple and the technology industry, given that they obviously are involved in interstate commerce. So now it seems like a slam-dunk case for the federal government, right? Not so fast. Finally we have arrived at the crux of the situation and why Apple has a chance to make history.
Apple vs The Commerce Clause
As United States v. Lopez showed, the Supreme Court seems willing to roll back some of the authority the federal government has claimed under the interstate commerce clause. This case was decided in 1995, which was at the dawn of the Internet going mainstream. In 2016 and beyond, Apple could certainly use the power of the Internet to shine light on the absurd Wickard v. Filburn ruling. Apple actually has a chance to take this case to the Supreme Court and have Wickard v. Filburn overturned! This is no small matter! In my opinion, it would rank up there with Brown v. Board of Education of Topeka which overturned the earlier Plessy v. Ferguson decision of “separate but equal.” The impact that case had on civil rights could be the same type of impact that overturning Wickard v. Filburn could have on privacy rights in this country. It would significantly hamper the ability of the federal government to arbitrarily infringe on our rights by strong-arming the companies that make our technology products, making it a major victory for privacy rights and freedom.
Now let’s be clear, Apple may have no interest in taking on the Herculean challenge of overturning Wickard v. Filburn. It would certainly be no easy road to travel. Apple would make a lot of enemies among those who benefit from establishment politics, which is to say they would piss off a lot of very powerful people. This may not be something Apple wants to tackle, being that they are not in the business of government reform. It may not exactly be profitable for Apple to take on the full force of the federal government.
However, that being said, there may be no one in a better position to overturn Wickard v. Filburn than Apple. They have several things going for them that together could create just the right circumstances for this historic turn of events. First, Apple has a lot of cash – a ridiculous amount of cash. This is usually the primary requirement for mounting a legal challenge against the federal government. Second, Apple is an extremely popular company. The public is not likely to stand by idly if the federal government tries to bully Apple in their quest to protect our privacy rights. No one wants to see a company as iconically American as Apple get taken down by the federal government. Thirdly, the privacy rights that Apple would be fighting for also seem to be extremely popular among the general public and especially among the Internet-connected younger demographics. Public support could definitely sway the political winds as it has done a few times in the Internet/social media era.
Even with some potential advantages, Apple has to want to fight this fight. They have every practical reason not to push the federal government that far, settling for a smaller victory along the way. But I think they just might be driven enough to eventually take on the misapplication of the Commerce Clause if the federal government continues to try to regulate the technology industry. While most may think of Apple as a technology company, those of us who have studied Apple know that Apple’s mission has always been to change the world. Steve Jobs did not want to start a business just to sell products, he wanted to make products that were going to transform society. It just so happened that technology was the avenue he saw to make that happen. Yes, Steve Jobs is gone, but his legacy is instilled in the corporate culture of Apple. Based on what I’ve seen from Tim Cook, his intensity in fighting this battle is a bit out of character for him. Perhaps he has found a cause worth publicly fighting for. This may be Tim Cook’s chance to change the world and leave a lasting legacy. It’s now up to him and Apple to make that choice.
Apple’s Security Can be Bypassed?
 A judge has ordered Apple to comply with the FBI’s request to bypass the security features of an iPhone used by a San Bernadino terrorist. In an open letter, Apple CEO Tim Cook has explained that what the government is requesting threatens the security of all their customers. In effect, the FBI admits that they can not decrypt the data on an iPhone without knowing the phone’s passcode. The FBI knows that not even Apple can decrypt the data, however, they have surmised that if they can load a version of the iOS that does not include certain security features that defeat brute force password attacks, then they can crack the passcode, which might only take minutes in a best case scenario. They claim Apple can create a version of the iOS without these security features, load it on the iPhone in question, and then the FBI can attempt to brute-force guess the password.
A judge has ordered Apple to comply with the FBI’s request to bypass the security features of an iPhone used by a San Bernadino terrorist. In an open letter, Apple CEO Tim Cook has explained that what the government is requesting threatens the security of all their customers. In effect, the FBI admits that they can not decrypt the data on an iPhone without knowing the phone’s passcode. The FBI knows that not even Apple can decrypt the data, however, they have surmised that if they can load a version of the iOS that does not include certain security features that defeat brute force password attacks, then they can crack the passcode, which might only take minutes in a best case scenario. They claim Apple can create a version of the iOS without these security features, load it on the iPhone in question, and then the FBI can attempt to brute-force guess the password.
Technology experts are warning that if Apple is forced to comply with this order it would have far-reaching consequences for the technology industry, privacy, and security. I am of the mind that the federal government does not have this authority at all, either at the legislative or executive level, much less a federal magistrate of a US District Court in California. It is an unreasonable, overreaching request of a technology company to share a method of bypassing security features in their own product. But there is plenty of discussion of that already. The question I’m surprised so few are asking is why the possibility even exists for Apple to defeat their own security functions?
The key point to consider is that the magistrate conceded that the FBI’s request may not be technically feasible and allowed Apple to respond if that is the case. Instead of stating that this request just isn’t technically possible as Apple has done in the past with other law enforcement requests, Tim Cook instead has vowed to fight this order. Which to me seems to imply that Apple COULD comply with the order. I found one article that describes a technically workable process by which Apple could comply with the FBI’s request. The article does speculate that newer iOS devices with a feature called the Secure Enclave may not be able to be hacked into in the process the FBI is requesting, but that is not certain. The iPhone 5C in question does NOT contain the Secure Enclave feature so that point is moot in this particular case, yet it does call into question the overall security of older iPhones and possibly newer iPhones pending the question of the security hardness of the Secure Enclave feature.
The reality is this: if Apple can technically comply with the FBI’s request, it means that a backdoor to iPhone security does, in fact, exist. Yes, it is a closely guarded secret by Apple, but in theory, this backdoor could be exploited if the secret key that Apple uses to sign their iOS updates is compromised. I would like to hear more about this from experts more versed in this topic than I am as well as an explanation from Apple if this backdoor does in fact exist.
Despondent Government Vexed by Encryption
The following is an article that I had been working on for some time. I’ve been editing and adding to this article to try to get it “just right” for several months now. However, with the situation Apple is facing today, I’ve decided that I must release this article now. So please forgive me if this article isn’t quite fully polished or rambles at times, but I felt that the core message had to be shared ASAP.
 It’s an issue that has been brewing over the last year-and-a-half. When Apple introduced iOS 8 in the fall of 2014, one particular feature had privacy advocates cheering. That same feature had certain law enforcement officials seething. With the release of with iOS 8, all data on an iPhone or iPad is encrypted when the devices are locked with a passcode. Not only that, but the type of encryption used by Apple is not able to be bypassed, even by Apple themselves. This means that even with a lawful search warrant or court order, Apple can not extract data from any iOS device to provide to law enforcement. In addition, the transmission of certain data, such as iMessages and FaceTime calls, are encrypted from end-to-end, which means that those forms of communication are not able to be intercepted by anyone, including Apple or law enforcement.
It’s an issue that has been brewing over the last year-and-a-half. When Apple introduced iOS 8 in the fall of 2014, one particular feature had privacy advocates cheering. That same feature had certain law enforcement officials seething. With the release of with iOS 8, all data on an iPhone or iPad is encrypted when the devices are locked with a passcode. Not only that, but the type of encryption used by Apple is not able to be bypassed, even by Apple themselves. This means that even with a lawful search warrant or court order, Apple can not extract data from any iOS device to provide to law enforcement. In addition, the transmission of certain data, such as iMessages and FaceTime calls, are encrypted from end-to-end, which means that those forms of communication are not able to be intercepted by anyone, including Apple or law enforcement.
At the time Apple introduced the new encryption feature, FBI director James Comey criticized both Apple and Google for using encryption technologies that were not able to be broken into by law enforcement. Apple CEO Tim Cook responded in early 2015 by saying that Apple had no intention of preventing people from encrypting their devices, in other words saying “tough luck” to government. The issue heated up last summer as the FBI director testified during a hearing of the US Senate Intelligence Committee, calling into question the idea that there is no way to create a encryption system that can be circumvented by manufacturers or law enforcement. He and representatives from the Obama administration’s Department of Justice hinted that if technology companies were not willing to cooperate in creating encryption with backdoor access, legislation may be required to force them to comply. In September, Apple formally declined compliance with a federal court order requiring them to turn over real-time messaging between suspects using iMessage, stating that they could not break the encryption technology used. All this was before the terror attacks of Paris and San Bernadino where once again law enforcement officials blamed technology companies for making it impossible for law enforcement to intercept communications or retrieve data from devices. More recently, Tim Cook strongly criticized the Obama administration for not issuing a strong public statement defending the use of strong encryption. Finally, a recently proposed bill in the the New York state assembly seeks to ban the sale of smartphones that do not provide an encryption backdoor. Update: A judge has ordered Apple to create a “hacked” version of the iOS that would bypass the security features that defeat brute force password attempts on an iPhone for use on the particular iPhone of a San Bernadino terrorist. More on this new situation in my next article.
The Poor Government is Just Beside Itself
The government is admitting that publicly available encryption technologies are thwarting their efforts to intercept communications or gather evidence. Current encryption protocols are so good that there is simply no feasible way for government agencies to break them, even with gobs of cutting-edge technology at their fingertips. So they are “kindly” asking technology companies to give them a back door and pushing lawmakers to pass new laws that would not-so-kindly force technology companies to use encryption that can be circumvented. They claim that without the ability to decrypt communications and data, they will be hampered in their ability to investigate terrorists and people will die. Oh, and kidnappers will also run willy nilly and kids will suffer horribly and they will die too. Don’t forget about the kids.
During the Senate hearing in the summer of 2015, several senators seemed shocked and awed that law enforcement couldn’t decrypt modern communications. Some agreed with the FBI and DOJ that legislation may be necessary. Others wondered if technology companies could be help in contempt. Senator John McCain even suggested that technology companies should give the government a special stockpile of encryption keys that could be used to decrypt any data or communication on their devices. “What’s the problem with that?” he asked.
But, But, But … the Fourth Amendment!
It would be funny how politicians twist the meaning of the Constitution if it wasn’t so sad. Some in government argue that the Fourth Amendment “allows” for reasonable search and seizure. Therefore creating laws (or taking executive actions?) that force technology companies to use encryption protocols with backdoors for law enforcement must be “reasonable.” It is humorous to hear otherwise “conservative” politicians argue that the Fourth amendment gives the government authority to define for itself the parameters of reasonable search and seizures. This is clearly a situation where some members of the supposed party of small government have no clue what small government really means.
Let’s take a moment and read the actual text of the Fourth Amendment:
The right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures, shall not be violated, and no Warrants shall issue, but upon probable cause, supported by Oath or affirmation, and particularly describing the place to be searched, and the persons or things to be seized.
Hmmm … looking over that text it does not state anywhere that the government is given the authority for “reasonable search and seizure,” nor that they can define what that means. Here’s your constitutional lesson of the day: the Fourth Amendment does not confer any power upon the federal government. Not a single one. It only serves to protect “the right of the people to be secure in their persons, houses, papers, and effects, against unreasonable searches and seizures.” It is not meant to grant power, as many politicians would try to argue, but rather meant to strictly limit the power of government. It is a guarantee against unreasonable search and seizures, not a license for the federal government to define what is reasonable and unreasonable.
The Convenience of Law Enforcement Does Not Override Our Freedoms
Even if we assume for a moment that the federal government has the authority to perform reasonable search and seizures, nowhere in the Constitution is the federal government given the authority to regulate encryption technology, nor dictate how companies offer products or services in the chance that they would need to perform a criminal investigation. If government has the authority to ask for warrants to investigate something, it is not the same as having the authority to require that they MUST be able to decrypt communications or data. That power would be analogous to the federal government requiring that all lock makers must give the federal government a way to easily pick their locks – just in case they need to investigate something that is locked up by a suspected criminal. If law enforcement has the means to decrypt communications or data, that’s fine (in this context), but if they don’t, then that’s too bad. Our freedoms are not subject to the convenience of law enforcement.
The Government Can’t Keep Anything Safe
Finally, if we were to go so far as to allow the federal government to have backdoor access into encryption technologies, do we have faith that they would not abuse this privilege? Or do we trust that they could keep the backdoor keys safe from criminals and other governments?
Edward Snowden pretty much blew out of the water the fantasy that government does not seriously exploit its authority. Besides the documented blatant abuses of the NSA, we also have government agencies like the IRS that can’t handle running a simple e-mail server correctly and secretaries of state that claim they can’t handle more than one mobile device. The purported lack of technology knowledge in both of these instances led to the all-too-convenient loss of communications that might have implicated government officials that were abusing their power. It was either intentional deception by government officials or cases of “innocence by incompetence.” Either way, this should not give anyone the warm and fuzzies for the ability of government to handle technology security. If certain people and agencies are given the power to decrypt the private communications of virtually anyone in the world, just how long do you think it will take for that authority to be abused or mishandled?
Also for a moment imagine just how valuable backdoor decryption keys would be. Anyone who had possession of them would be able to pry into just about anyone’s private lives, blackmail and extort people, and steal corporate secrets just to name a few things. Backdoor encryption keys would be likely the most valuable pieces of information the world has ever known!
We know humans are not perfect. How much money do you think criminal organizations or other governments would pay to bribe the keepers of the keys? That number would probably be astronomical and it would be hard for anyone to not consider taking a bribe like that. Even if we completely trust the people who would handle these incredibly valuable pieces of information right now, what’s to say the next people in line won’t be corruptible?
Finally, even if we assume that those who have guard the backdoor encryption keys will be paragons of morality, those secrets will be the most sought-after data the world has ever known. Criminals and governments would likely stop at nothing to steal them. The federal government can’t even keep hackers from stealing information on tens of thousands of government employees, do we honestly think they’ll be able to keep the keys to our private data safe?
The Government Doesn’t Care about YOUR Privacy
If you want a more concrete example about the lack of the ability of government to keep your privacy safe, take the TSA. The federal government forces air travelers to only use TSA-approved locks on their luggage. The TSA has access to special “master keys” that can open any TSA-approved lock. What would happen if the patterns to those master keys were compromised and leaked out into the public? Then anyone could create a copy of keys that could open a traveler’s luggage without leaving proof of the break-in. Of course that would never happen because the TSA would take extreme caution with those sets of master keys, right? Wrong. The seven master TSA keys have been compromised and anyone with a 3D printer can create a set of keys that will open any TSA-approved lock. And guess what? The TSA couldn’t care less that YOUR privacy and security has been compromised, as long as they can still open your luggage.
Now granted, when luggage travels through various airports, one should not expect that the contents of that luggage is truly secure. So this appalling failure of the federal government is not truly that big of a deal in the grand scheme of things. However, this does spotlight that no system of backdoor access can be trusted to stay secure, even if agencies specifically tasked with security are handling them. One could probably count with an egg timer how long it would take for the proposed backdoor keys for encryption to be compromised. Even worse, most of us probably wouldn’t even know they had been compromised because it would be in the best interest of those with the keys to not publicize the fact that they had them.
It’s Time to Stand Up
The idea that privacy must be balanced against security is a red herring argument. At best it is government being lazy. At worst it is government creating convenient excuses to grab themselves the legal authority to infringe on our privacy. Again, our rights are not subject to the convenience of government. Additionally the government must prove their authority to exercise a specific power, of which forcing the types of encryption technologies we the people can use is not one of them.
For far too long the government has assumed that just because a specific guarantee to a “right to privacy” doesn’t exist in the Constitution, then they have the power to trample over our unalienable privacy rights. Of course, the 9th and 10th amendments prove them wrong, but until enough of us demand that the government follow their own laws, their might makes right. The good news is that technology has developed to a point where we can take measures to protect our own privacy rights even from government. We must fight against any attempt by government to deny, circumvent, or ban these technologies because as we’ve seen, government is one of the worst infringers of our rights – and their meddling would make us all much less secure from anyone with bad intentions.